Acceleration through Simulation
Precision and speed with modular quantum chemistry and machine learning pipelines for pharmaceuticals, materials, and chemistry.
Develop breakthrough compounds and manufacturing in days, not months.
Cebule™ - Pay per Usage
Database, Engine, Agent and Compute Provision
Pricing
25 minutes for free
700 minutes for 50$ (40€)
2500 minutes for 150$ (130€)
6000 minutes for 300$ (260€)
Cebule™ - Enterprise
Cloud/On-premise + Optional European HPC Provision
Select Features
AWS, Azure, Google Cloud deployment (other providers also supported)
On-premise or supercomputer HPC connection capabilities
Quantum computing integration
Automated lab connection
Discover the available tools in the Cebule™ Platform
Ready to revolutionize your research workflow? The Cebule™ Platform offers a visual interface to search through quantum chemistry data of over 200 million molecules. On top of the advanced search capabilities, the Cebule™ Compute Engine, JupyterLab and Kubeflow are integrated with the Cebule™ HPC to leverage high performance CPUs, GPUs and QPUs.
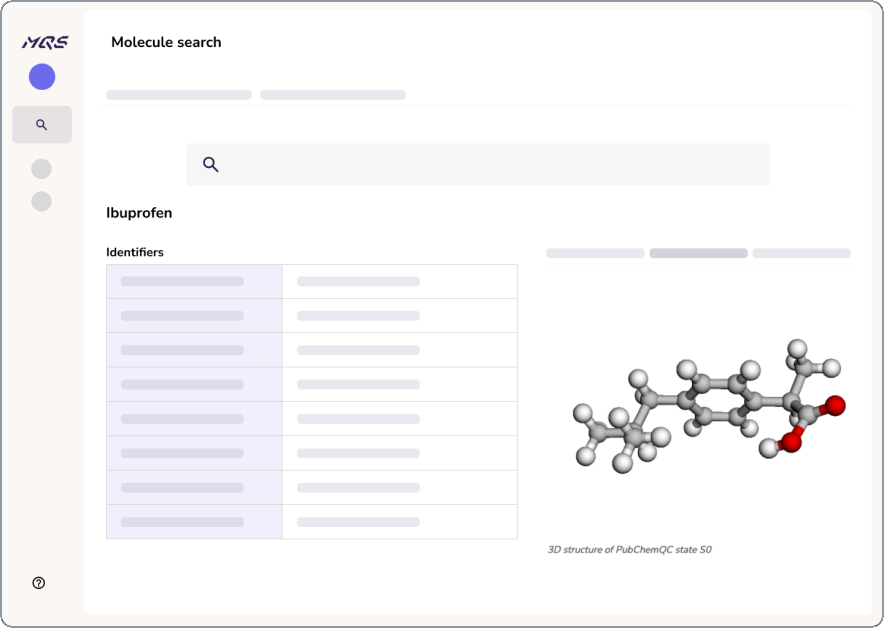
Over 200 million molecules Searchable PubChemQC PM6 and QMugs datasets
High performance compute infrastructure JupyterLab and Kubeflow support
Accelerate and scale your research with optimised HPC Infrastructure
The high performance computing infrastructure can be seamlessly integrated with your own technology stack. Create modular and well-defined quantum chemistry, AI and quantum computing pipelines via MLOps and utilise the Cebule™ HPC.
The Cebule™ Python SDK allows you to easily send off calculations to a hybrid cloud infrastructure including also SLURM and on-premise setups.
Partners & Networks
Calculate.
Apply high-performance quantum chemistry and molecular dynamics to calculate molecular target properties.
Find.
Find promising molecular systems and define a design of experiments for the laboratory.
Develop.
Combine in-silico and experimental data sets to perform modern R&D with Bayesian closed-loop optimisation.
Learn about the Cebule™ Platform
Whether you are a quantum chemist, experimentalist or engineer, the Cebule™ SDK and user interfaces enhance your workflow with access to molecular data. algorithms and high-performance infrastructure. In combination with JupyterLab and Kubeflow you are able to make use of a coding environment and MLOps without any setup overhead.
Overview >>
Dashboards >>
Software Development Kit (SDK) >>
Database & Datasets >>
Partnering
Partner with MQS to start a collaborative project to apply our software tools and experimental validation for the pharmaceutical, crop science, chemical and material industries.


Testimonials
"The workshop was just perfect introduction into the universe of quantum computing. Not only a few first steps, but a massive boost that I will profit from in years to come ..." Dr. Martin Friak, Group Leader at Institute of Physics of Materials Academy of Sciences of the Czech Republic "The MQS workshop resurrected the dead quantum mechanics I had learned during my bachelor's degree, and simultaneously, connected with myself back, opening a window where quantum computers could be utilized for my research." Dr. Hyun-Jung Kim, formerly Forschungszentrum Jüllich, now LGDisplay "Being new to quantum computing I found this workshop very useful. It was very well organized and the practical exercises in the afternoon helped me a lot getting started investigating the possibilities of using quantum computers within my field of research." Prof. Jacob Kongsted, University of Southern Denmark (SDU) "The workshop provided an excellent introduction to the theoretical basics and hands-on exercises needed to jump into quantum computing." Dr. Siddhant Agarwal, Deutsches Zentrum für Luft- und Raumfahrt (German Aerospace Center) "I had the pleasure to participate in the first Quantum Computing Workshop organized by MQS and it was a time well spent. Starting from the fundamentals of quantum computers they brought us up to applications both within quantum chemistry and machine learning. In addition to inspiring lectures, they had also organized relevant hands-on exercises, where we were guided to write our first small programs for a quantum computer using the Pennylane library. I will certainly consider to send my students, the next time they offer the course again." Prof. Stephan Sauer, Copenhagen University




Day 1: Basic Theory and Overview
- Introduction to basic theory including:
- Recap of necessary linear algebra and quantum mechanics
- Fundamentals of quantum computing – states, gates, measurements, quantum algorithms, quantum circuits, design principles, how and when to formulate real world problems for quantum computers
- Overview of state-of-the-art hardware technology: superconducting, photonic, trapped ion, neutral atom
- Quantum Annealing & Digital Annealing
- Quantum Approximate Optimization Algorithm (QAOA)
Day 2: Quantum Chemistry & Variational Quantum Algorithms
- Introduction and overview of variational quantum algorithms
- Working principle of VQE algorithms and how they are designed
- Overview of existing variants of VQE algorithms
- Simple examples for finding ground state energy of a small molecule
- Capabilities and limitations of VQE algorithms in theory and practice
Day 3: Quantum Machine Learning (QML) & Tensor Networks
- Introduction to QML and its relation to conventional machine learning
- Introduction to quantum differentiable programming and applications
- Quantum generative adversarial networks via quantum computing
- Convolutional neural networks via quantum computing
- Tensor networks
Day 4: Fault Tolerant Quantum Computing
- Introduction to FTQC
- Hardware – how far are we?
- Quantum error correction
- FTQ algorithms and applications
- Loading classical data into quantum algorithms
- Quantum memory – QROM, QRAM
- State preparation and unitary synthesis
- Block encodings
- Hamiltonian simulation
- Phase estimation
- Latest developments in the field
Theory and code exercises include the following topics:
- Define and visualize a quantum state on the Bloch sphere
- Cartesian to polar form conversion; Polar to cartesian form conversion
- Braket notation and linear algebra
- Creating quantum circuits
- Measuring qubits
- Understanding 1-,2-, 3-qubit quantum gates; Toffoli gates; Universal quantum gates
- Pure and mixed states
- Adapting to quantum hardware topology
- Basic quantum computing methods/algorithms
- Quantum and digital annealing
- Variational quantum algorithms (VQA)
- Parameterized quantum circuits for quantum machine learning (QML) and with tensor networks
- Classifying via QML
- Quantum convolutional neural network
- General adversial network (GAN) and Quantum GAN
Our Team
The MQS team members are highly-interdiscplinary working at the intersection of quantum chemistry, quantum computing, chemical engineering, computer science, digital transformation and laboratory automation.
Mark Nicholas Jones
CEO/CTO, Co-founder
Kurt Stokbro
Co-founder, Investor, Chairman of the Board
Kristín Björg Arnardóttir
Lead for Quantum Technology Development
Kaur Kristjuhan
Quantum Computing Methods Developer and Industrial PhD
Andreas Klamt
COSMO Expert Advisor
Patrik Ando
DevOps Engineer and Computer Scientist
Miguel Alonso
Scientific Developer
Clara Ferreira Cores
Researcher & Multi-disciplinary Artist (Art, Science & Philosophy)
Lykke Sophie Stokholm
Projects Coordinator & Management Support
Szabolcs Ducza
UI and Web Designer
Stine Rønholt
Scientific Advisor
Dominic Berry
Scientific Advisor
Stephan Sauer
Scientific Advisor
Mie Kristensen
Scientific Advisor
Peter Reinholdt
Scientific Advisor
Joachim Schelde
Member of the Board
Lars Jensen
Observer of the Board
What is Quantum Computing?
Some important historic evolution steps of the idea and development of a quantum computer (1959-1984)
Richard P. Feynman is regarded as the person who sparked the idea of a quantum computer with his talk titled "There is Plenty of Room at the Bottom" given at the American Physical Society in Pasadena (December 1959).
A transcript from his talk "There's Plenty Room at the Bottom" conveys Feynman's physical notion of information storage from a volumetric perspective and depicts DNA as an example, where "around 50 atoms are used for one bit of information about the cell". Then Feynman describes how small computers could be built and fabricating electric circuits on the atomistic level although resistance would be a problem. The problem, Feynman mentions, could be solved through the use of superconductivity. At this scale, building a computer with atoms becomes quantum mechanically defined and "We can use, not just circuits, but some system involving the quantized energy levels, or the interactions of quantized spins, etc.". Although Feynman does not use the term "quantum computer" one can already see the vision and follow the line of thought he had.
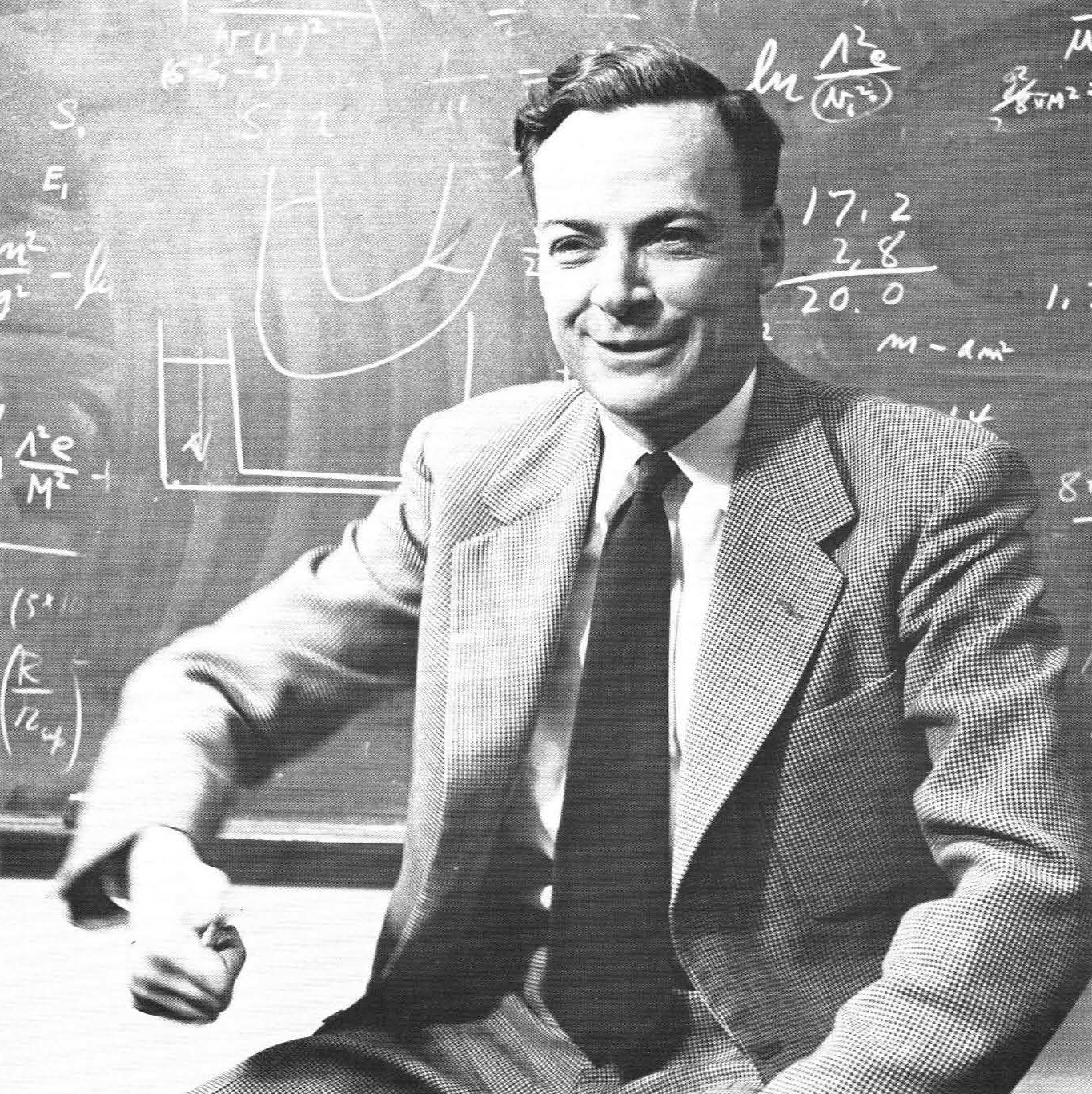

David Finkelstein acknowledged in his "Space-time Structure in High Energy Interactions" article that it was Feynman who introduced him to the idea that space-time should be quantum mechanically discretized and in this way a "reasonable model for the world is a computer, a giant digital computer" would allow more advanced computations.
In 1979 Paul Benioff constructed a quantum mechanical model of computers where the evolution of a Hamiltonian (energy function) would represent a closed conservative system. Benioff showed in the article "The computer as a physical system: a microscopic quantum mechanical hamiltonian model of computers as represented by Turing machines" that this quantum mechanical model can be calculated by a set of Turing machines which themselves are stationary systems, but collectively, these processing units can simulate dynamic systems.
Richard Feynman's description of how to accurately calculate quantum physical systems on a quantum computer architecture can be seen as the first description of a quantum computer architecture. He submitted the description on the 7th of May 1981 to the International Journal of Theoretical Physics. The article was then published in volume 21, June, 1982. Together with Richard Feynman, David Deutsch is regarded as the father of the idea and detailed description of a quantum computer. David Deutsch described in 1985 his idea of an universal quantum computer. In the proceedings paper "The church–turing principle and the universal quantum computer" he describes a computing machine with a quantum physical architecture and that it can have many remarkable properties which cannot be found in Turing machines. Further, David Deutsch proved also with the Deutsch and Deutsch-Josza algorithm that a quantum computer can give an advantageous speed up in comparison to a classical computing scheme.
Quantum supremacy and quantum advantage
Quantum computing has been studied for decades and ranges from information theory to hardware technologies, computational models implemented on specific hardware types which go hand in hand with the mathematical problem formulations being solved on the quantum device.
It has applications in nearly every field that contains or utilizes computations with high complexity. Quantum computers have the potential to impact many aspects of current domains of science, including computer science, mathematics, and chemical engineering. Generally, to compare the performance of classical computing and quantum computing is not an easy task and several scenarios exist how a quantum computer could be utilized for the benefit of research or solving societal important problems which a classical computer alone could not solve due to the problem's NP-hard complexity.
A desirable scenario is one where problems that can not be solved by classical computers in any feasible amount of time, would be possibly solved with a quantum computer. This is one of the main goals of quantum computing, which is termed quantum supremacy. It is a demonstration that a programmable quantum device can solve a problem that any existing or future classical computer is not able to solve due to the problem's NP-hard complexity.
A second scenario is related to computational problems which could be solved more efficiently with both classical computers and quantum computers together, although not ruling out that a classical algorithm could solve the problem as efficienctly as the hybrid classical-quantum scheme when more powerful classical processing units would be available or a better classical algorithm is discovered.
The third category is comprised of problems that can not be solved more efficiently with a quantum computer. Thus, a careful analysis of the mathematical complexity of a mathematical problem formulation must be made to assess which computational system/architecture should be applied.
John Preskill published a paper titled "Quantum computing and the entanglement frontier" in November 2012 about quantum supremacy and the consequences it will have to several critical applications in society such as cryptography and optimization.
In October 2019, Google claimed with the Nature article "Quantum supremacy using a programmable superconducting processor" " to have achieved supremacy with a quantum processor called "Sycamore" to sample the output of a pseudo-random quantum circuit. They used 53 qubits to represent a dimensional state space.
Measurements from repeated quantum experiments sampled the resulting probability distribution, which then was verified using classical simulations. The process of sampling one instance of a quantum circuit a million times took about 200 seconds. With a classical computer that process would have taken 10,000 years. However, IBM stated with the blog post 'On "quantum supremacy"' that the computation of the Google experiment could be performed on a classical computer in 2.5 days. Many more quantum supremacy claims and demonstrations were made and the below table gives an overview of some of them.
| Google (2019) | USTC (2020) | USTC (2021) | Xanadu (2022) | |
|---|---|---|---|---|
| Mathematical problem | Linear cross-entropy benchmarking fidelity of a pseudo-random quantum circuit | Gaussian Boson Sampling | Two-dimensional programmable quantum walks | Gaussian Boson Sampling |
| Device | Superconducting transmon (Sycamore) | Optical interferometric network (Jiuzhang 2.0) | Superconducting transmon (Zuchonzhi 2.1) | Photonic processor (Borealis) |
| Results/Claims | 200 seconds to sample one instance of a quantum circuit a million times in comparison to 200 million years classically | Measured sampling rate about 1014-fold faster than state-of-the-art classical method | Classical algorithm takes about 4.8x104 years while Zuchongzhi 2.1 takes about 4.2 hours | 9000 years for best classical algorithm to generate a single sample from programmed distribution, the quantum algorithm took 36 |
You can learn more about quantum computing for chemistry topics by signing up for the Dashboard Quantum or Machine Learning subscriptions.